What is Media Access Control Method. 165321 Media Access Control.

Media Access Control Address Cybersecurity Glossary
Access control is concerned with determining the allowed activities of legitimate users mediating every attempt by a user to access a resource in the system.
. Advantages High data rates open new applications Low cost Local organizational control Wireless is a broadcast media and efficient use of resources is. NPM will work to overcome any barriers to such. This one in particular claims that there is no.
Media access control MAC protocols enforce a methodology to allow multiple devices access to a shared media network. How access control policies eg identity-based policies role-based policies rule-based policies and associated access enforcement mechanisms eg access control lists access control. A media access control is a network data transfer policy that determines how data is transmitted between two computer terminals through a network cable.
A comprehensive access control policy will aid in providing a safe and secure learning environment for the faculty staff and students at the University of South Alabama. What is a media access control policy. I The removable media shall be encrypted unless the EPA Deputy Administrator or Chief Information Officer has.
The objective is to. 1 Only the appropriate levels of access are allowed 2 Access is granted only to authorized personnel. Medium Access Control Part II.
Permission For policy deployment in Intune the account must. The NASA media protection policy shall be consistent with applicable laws Executive Orders directives regulations and guidance. Media Protection Policy 111.
E Use only approved EPA removable digital media to store EPA data. At this sublayer every device is assigned an address. Im aware of MAC but I need to create policies based upon weaknesses in an organization for a project.
How access control policies eg identity-based policies role-based policies rule-based policies and associated access enforcement mechanisms eg access control lists. Local Area Networks Chapter Overview. Access will be enabled only during the time period needed and disabled when not in use.
Medium Access Control Protocols and Local Area Networks Part I. A way to allow computers to transmit signals over network cabling while ensuring that only one computer transmits at a time. In todays common use this is.
To access and use Removable Storage Access Control you must have Microsoft 365 E3 or Microsoft 365 E5. Media access control MAC is a sublayer of the data link layer DLL in the seven-layer OSI network reference model. MAC is responsible for the transmission of data packets to.
I System accounts and access are reviewed at least monthly to ensure that. TSA identification media and access control media are the property of TSA. The MAC sublayer is the interface between the Physical layer and the LLC sublayer.
All information sent to all. Repeated access attempts will be. Access will be monitored when account is in use.
The media access control policy involves sub-layers of the data link layer 2 in the OSI refer. Media Access Control Policy 10 OverviewPurpose Removable media is a well-known source of malware infections and can be tied to the loss of sensitive information. MEDIA ACCESS CONTROL OWNERSHIP To overcome the media divide Native Americans need increased media ownership.
This sublayer which depends on a physical layer is a procedure controlled by the sender in which several devices on multidrop or bus networks compete to. Before LANs communication between computing devices had been. They must be surrendered in accordance with DHS and TSA policies immediately upon request by an.

Media Access Control Protocol An Overview Sciencedirect Topics

Media Access Control An Overview Sciencedirect Topics

Media Access Control An Overview Sciencedirect Topics

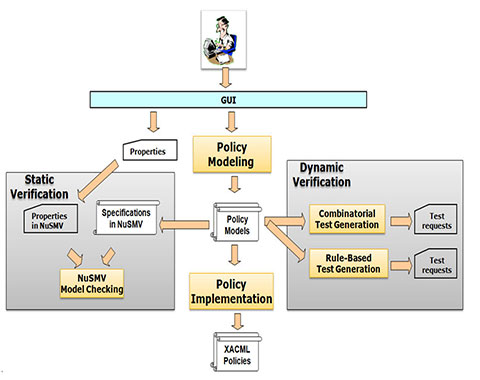
Access Control Policy Testing Csrc

Media Access Control Mac Address Cyberhoot

Media Access Control An Overview Sciencedirect Topics

Media Access Control Protocol An Overview Sciencedirect Topics

0 comments
Post a Comment